Mimecast: Encryption Requirements for HIPAA Compliance
Roadtrippers Helps Travelers Plan Budget-Friendly Road Trips
Telesystem to Acquire Cybersecurity Provider Threat Protector
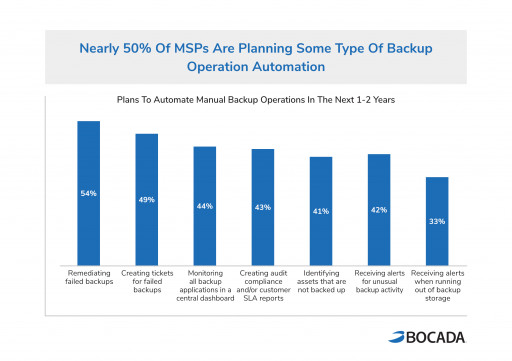
New Study Finds MSPs Leveraging Automation to Overcome Backup Operations Challenges
5 Common Phishing Attacks to Watch Out for
So You’ve Been Phished. What Now?
iQuanti: Over two million domains are connected to phishing attacks. Unfortunately, with such a high number, it's difficult to avoid them if you aren't on the lookout.
What is phishing?
Phishing is a cyberattack where cybercriminals disguise themselves as legitimate organizations or other trusted entities to trick the target into providing private information like login credentials, credit card details, or even their social security number (SSN).
Personal risks to falling victim to phishing
- Money stolen from your bank account.
- Fraudulent credit card charges.
- Loss of access to personal files, including photos and videos.
- Identity theft where cybercriminals impersonate you to friends or family, putting them at risk.
Risks to your business:
- Loss of corporate funds.
- Exposing customers' and coworkers' personal details.
- Loss of data.
- Reputational damage to your company.
You clicked a link in a phishing email by accident
First, if you receive a suspicious message, you should not open any links or attachments within the message. If you already clicked the link, you were likely redirected to a web page where you are prompted to fill in sensitive information like credit card details or your SSN. Do not enter these details, as they will go directly to the attacker for personal gain.
If you have gone beyond clicking the link or attachment and accidentally entered your information, you should conduct a full malware review of your device and system.
Once you have completed the scan, back up your files and change your passwords; even though you may not have given away those details, you may have inadvertently given the attackers enough leeway to obtain other personal identifiers.
Simple next steps if you think you may be the victim of a phishing scam
- When you doubt a message from a seemingly legitimate organization, contact the organization that supposedly emailed you instead of responding or interacting directly with the message.
- Scrutinize suspicious emails and messages. Check for spelling mistakes, faulty grammar, or a wrong-looking logo, which can indicate phishing.
- If you accidentally click a phishing link, close the page and do not input any details.
- Run virus scans and back up your files frequently.
Preventing phishing attacks
To protect against spam messages, you can use a spam filter that can effectively assess the message's origin and the software used to send the message. In addition, a spam filter may be able to determine whether a message is spam or not based on its appearance.
You can be proactive by changing your browser settings to prevent accidentally clicking on a fraudulent website. For example, when you set your browser to only allow reliable websites to open, the fraudulent address would be blocked - alerting you with a popup message.
Another way to ensure security is to change your password as frequently as every three months and don't use the same password on multiple accounts.
Final thoughts
The success of phishing attacks hinges on whether or not the target is educated on how these scams work. Therefore, the more cautious you are, the better protected you will be.
Press Release Service by Newswire.com
Original Source: So You've Been Phished. What Now?
Phishing: What is It?
Mimecast: How to Protect One’s Crypto From Phishing
Cybercriminals have targeted the cryptocurrency community since bitcoin's inception, and many crypto owners are falling prey to schemes like phishing.
What is phishing?
Phishing is a digital crime where cybercriminals aim to steal a user's private information. Scammers deploy their attack by disguising themselves as trusted organizations or entities to trick a user into mindlessly handing over details like their Social Security number, credit card information, bank credentials, and in this case, crypto wallet details.
Use Multi-factor authentication
There is no surefire way to keep cybercriminals from attempting to breach an organization's system. However, it is possible to make it harder for attackers to succeed in obtaining sensitive information. Multi-factor authentication (MFA) is an easy passive approach for users to secure their crypto wallets.
MFA adds an extra layer of protection on top of passwords for both an organization and an employee. So, a password will not be enough even if a user falls victim to a phishing scam.
Avoid fraudulent emails
Remember, if something looks too good, it probably is. Over 270,000 Ledger wallet users had their emails extracted in 2020. Phishing attacks, like the breach against Ledger users, promise free wallets that are secretly compromised.
Messages that are urgent or prompt a speedy response may also be phishing scams. Other phishing messages may state that if a user does not act now, their account with whatever legitimate organization the attackers are impersonating will be suspended.
Most reliable companies will offer ample time for customers to get their affairs in order. However, it is best to ignore such messages as this is a favorite method for cybercriminals. When in doubt, contact the source directly to clarify the matter instead of interacting with the potentially fraudulent message.
Also, users should scrutinize emails with a sharp eye — especially ones with such grand requests and promises. Keeping an eye on the email's domain and checking for spelling mistakes could be the telltale signs a user needs to identify the phishing scam.
Keep the private keys secure
Users must keep their private keys, the line of letters and numbers used to access their cryptocurrency that resembles a password, private.
A user's private key is something that they should never disclose.
Use an email filter
To protect against spam messages, users and organizations can use a spam filter that can effectively assess the message's origin and the software used to send the message. In addition, a spam filter may determine whether a message is spam or not based on its appearance.
Email filters are the first line of defense against phishing scams of all sorts and will actively scan any emails going through a user's server for spam, malware, and malicious attachments and links.
Prepare! Prepare! Prepare!
The success of phishing attacks hangs on the preparedness and education of the target. Security awareness training on how phishing scams work can go a long way in keeping a company's and a user's crypto safe.
Contact: [email protected]
Press Release Service by Newswire.com
Original Source: Mimecast: How to Protect One's Crypto From Phishing